Anyconnect Remote
KB ID 0000546
Problem
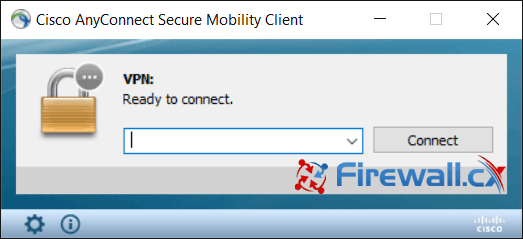
If you connect to to a client via RDP then try and run the AnyConnect client, you will see one of these errors;
VPN establishment capability for a remote user is disabled. A VPN connection will not be established
VPN establishment capability from a Remote Desktop is disabled. A VPN connection will not be established
EgtonN3/Cisco Anyconnect. The Cisco Annyconnect software has been updated. Then double click on the Install-emis-Secure-Remote-Access file. This video shows how to configure of AnyConnect Remote Access VPN on Firepower Threat Defense using FMC Linkedin: https://www.linkedin.com/in. Go to Configuration, Remote Access VPN, Anyconnect Client Profile Click Add and create a new profile and choose the Group Policy it should apply to Click OK, and then at the Profile screen click 'Apply' at the bottom (important). By default, only local users may connect via any connect client. You would need to edit the anyconnect client profile. Please change the WindowsVPNEstablishment parameter to 'AllowRemoteUsers' instead of 'LocalUsersOnly. After Changed to 'AllowRemoteUsers' what I have to do?
This, behaviour is default, and despite me trawling the internet to find a solution (most posts quote changing the local AnyConnectProfile.tmpl file, this file does not exist using Version 3 (I was using v 3.0.4235).
Update: With Early versions of AnyConnect version 4 it does not tell you what’s wrong, the VPN appears to connect and then disconnect quickly. If you have debugging on the firewall you will see the following;
Profile settings do not allow VPN initiation from a remote desktop.
Note: This is fixed in version 4.8 and you will se the error at the top of the page.
Solution
To solve this problem we need to create an AnyConnect profile, load the profile into the firewall, then associate that profile with your AnyConnect group policy. With modern versions of AnyConnect you can do that in the ASDM. With older versions you need to use the stand alone profile editor (see below)
Edit AnyConnect Profile With ASDM
Connect to the ADSM > Configuration > Remote Access VPN > Network Client remote Access > AnyConnect Client Profile.
Give the profile a name > Select a group policy to apply it to > OK.
AllowRemoteUsers: Lets remote users bring up the VPN, if this forces routing to disconnect you, it will auto terminate the VPN.
SingleLocalLogon: Allows multiple remote logons but only one local logon.
OR (older versions)
Apply the changes, and then save to the running configuration.
Edit AnyConnect Profile With Stand-Alone Profile Editor
1. First download the AnyConnect Profile Editor from Cisco. (Note: You will need a valid CCO account and a registered support agreement/SmartNet).
Update: The AnyConnect Profile Editor is now built into the ADSM, it becomes available once you have enabled any AnyConnect image. Once you have a profile created you can skip straight to step 3, and skip all the other steps.

If you cannot download the software here’s a profile (I’ve already created) you can use. If you are going to use this, jump to step 5.
2. Once you have installed the profile editor, launch the “VPN Profile Editor”.
3. The setting we want is listed under Windows VPN Establishment, and needs setting to “AllowRemoteUsers”, In addition I’m going to set Windows Logon Enforcement to “SingleLocalLogon”.
AllowRemoteUsers: Lets remote users bring up the VPN, if this forces routing to disconnect you, it will auto terminate the VPN.
SingleLocalLogon: Allows multiple remote logons but only one local logon.
4. Save the profile somewhere you can locate it quickly.
5. Connect to the firewalls ASDM > Tools > File Management > File Transfer > Between Local PC and Flash.
6. Browse your local PC for the profile you created earlier > Hit the “Right Arrow” to upload it > This can take a few minutes, depending on your proximity to the firewall.
7. Make sure the file uploads correctly > Close.
8. To associate this profile with your AnyConnect//SSL Group Policy, click Configuration > Remote Access VPN > Network (Client) Access > Group Policies > Locate the policy in use for your AnyConnect clients > Edit > Advanced > SSL VPN Client > Locate the “Client Profile to Download” section and uncheck the inherit button.
9. Click New > Browse Flash > Locate the profile you uploaded earlier.
10. OK > OK > Apply > Save the changes by clicking File > Save running configuration to flash.
11. Then reconnect with your AnyConnect Mobility Client software.
Related Articles, References, Credits, or External Links
Telework at VA
Telework is governed by VA Handbook 5011/26/31 Part II Chapter 4.
Employees working with their supervisor would need to determine telework suitability and eligibility to telework. Once determined telework eligible the employee would need to fill out VA Form 0740 Telework Agreement, the Telework Notification Letter – Employee Eligible to Telework, and you will need to complete Talent Management System (TMS) training as follows:
- All managers must complete TMS Course VA1366994 — Telework Training Module for Managers.
- All employees requesting telework must complete
- TMS Course VA1367006—Telework training module for employees
- TMS Course VA10176—VA Privacy and Information Security Awareness and Rules of Behavior
- TMS Course VA10203 Privacy and HIPAA Training
Additional information on telework can be found Office of Human Resources Management Telework webpage ( only available while on VA's internal network) and OPM’s Telework website.
VA Remote Access
VA Handbook 6500 identifies the compliance requirements for VA remote access users.
VA supports remote access with two different applications 1. Citrix Access Gateway (CAG) and 2. CISCO RESCUE VPN Client. The Citrix Access Gateway is designed for users that do not have VA Government Furnished Equipment (GFE) – CAG is a good option to allow users access to general applications such as email and chat. The CISCO RESCUE VPN Client is only for use on VA Government Furnished Equipment (GFE) and is installed on all GFE laptops. Users would still need to request remote access and have their remote access accounts enabled for use with either CAG or RESCUE.
You may request remote access by visiting the Remote Access Self Service Portal ( only available while on VA's internal network).
Please note the Self-Service Portal is only accessible from within the VA network, it is not externally accessible. If you require technical support, please reference the FAQs and other supporting documentation found at https://raportal.vpn.va.gov or contact the Enterprise Service Desk (855) 673-4357.
Software, supporting documentation, FAQs and general information are hosted at the VA’s Remote Access Information and Media Portal. Please ensure you have Transport Layer Security (TLS) 1.1 enabled on your web browser before attempting to access this site. To enable TLS within Internet Explorer: Select ‘Tools’, then ‘Internet Options’, then the ‘Advanced’ tab. Enable the checkbox for ‘Use TLS 1.1’ (found towards the end of the list).
Anyconnect Remote
How do users or facilities request equipment if they require VPN access?
- Click the “Your IT” Icon on your desktop or go to YourIT Services ( only available while on the VA’s internal network)
- Click “Make a Request”
- Click “Computer Services,” under categories
- Click on “OIT Equipment and Software”
- Complete all required fields.
- Tag request for COVID in “Justification,” field
Cisco Anyconnect Remote Desktop Disabled
If you do not require VPN, use the CAG process.
