Meraki Vpn Ipad
This article outlines instructions to configure a client VPN connection on commonly-used operating systems. For more information about client VPN, please refer to our Client VPN Overviewdocumentation.
For troubleshooting, please refer to our Troubleshooting Client VPN documentation.
I am using meraki cloud authentication. After some troubleshooting, it looks like the upstream Comcast router is causing the issue. We have a static, public IP on the MX, so I don't know why the router isn't forwarding correctly. Has anyone else here had problems with Comcast and Meraki RAS VPN? This has happened roughly 3 or 4 times. At first I will be able to push apps, communicate with all iPads, refresh profiles, etc. Slowly but surely the iPads will lose connectivity intermittently with meraki until at last they no longer communicate to the Meraki Dashboard indefinitely (no app push, profile push, notifications, etc). A Meraki VPN setup ipad is created away establishing a virtual point-to-point transferral through the use of consecrate circuits or with tunneling protocols over existing networks. Since we're keep in a connected world, security and privacy are critical to insure our personal birth control device from nefarious hacks. Cisco Meraki offers the only solution that provides unified management of mobile devices, Macs, PCs, and the entire network from a centralized dashboard. Enforce device security policies, deploy software and apps, and perform remote, live troubleshooting on thousands of managed devices. Copy another profile: Allows you to clone settings from an existing Meraki configuration profile in any of your organization's Systems Manager networks into a new profile. Note: Apple User Profiles will show as 'Missing' on the Device Details page if the Apple User Profile is pushed to iOS devices not using shared iPad configurations for Apple.
Android
To configure an Android device to connect to the Client VPN, follow these steps:
- Navigate to Settings -> Wireless & Networks -> VPN
- Click the Plus Icon to add an additional VPN profile
Name: This can be anything you want to name this connection, for example, 'Work VPN.'
Type: select L2TP/IPSEC PSK
Server address: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
IPSec pre-shared key: Enter the pre-shared key that admin created in Security appliance >Configure > Client VPN settings.
Press save
You will be prompted for user credentials when you connect.
Chrome OS
Chrome OS based devices can be configured to connect to the Client VPN feature on MX Security Appliances. This allows remote users to securely connect to the LAN. This article will cover how to configure the VPN connection on a Chrome OS device. For more information on how to setup the Client VPN feature of the MX or how to connect from other operating systems, please visit the MX documentation.
- If you haven't already, sign in to your Chromebook.
- Click the status area at the bottom of your screen, where your account picture is located.
- Select Settings.
- In the 'Internet connection' section, click Add connection.
- Select Add private network.
- In the box that appears, fill in the information below:
- Server hostname:Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- Service name: This can be anything you want to name this connection, for example, 'Work VPN.'
- Provider type: Select L2TP/IPsec + Pre-shared key.
- Pre-shared key: Enter shared secret that admin created in Security appliance >Configure > Client VPN settings.
- Username credentials for connecting to VPN. If using Meraki authentication, this will be an e-mail address.
- Password credentials for connecting to VPN.
- Click Connect.
For more information regarding the configuration of VPN connections in Chrome OS, visit the Google Support page.
To configure an iOS device to connect to the Client VPN, follow these steps:
- Navigate to Settings -> General-> VPN -> Add VPN Configuration...
- Type: set to L2TP.
- Description:This can be anything you want to name this connection, for example, 'Work VPN.'
- Server: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- Account: Enter the username
- Password: Enter if desired. If the password is left blank, it will need to be entered each time the device attempts to connect to the Client VPN.
- Secret: Enter shared secret that admin created in Security appliance >Configure > Client VPN settings.
- Ensure that Send All Traffic is set to On.
- Save the configuration.
macOS
Currently only the following authentication mechanisms are supported:
- User authentication: Active Directory (AD), RADIUS, or Meraki hosted authentication.
- Machine authentication: Preshared keys (a.k.a., shared secret).
When using Meraki hosted authentication, VPN account/user name setting on client devices (e.g., PC or Mac) is the user email address entered in the Dashboard.
The instructions below are tested on Mac OS 10.7.3 (Lion).
Open System Preferences > Network from Mac applications menu. Click the '+' button to create a new service, then select VPN as the interface type, and choose L2TP over IPsec from the pull-down menu.
- Server Address: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- Account Name: Enter the account name of the user (based on AD, RADIUS or Meraki Cloud authentication).
- User Authentication > Password: User password (based on AD, RADIUS or Meraki Cloud authentication).
- Machine Authentication > Shared Secret: Enter shared secret that admin created in Security appliance >Configure > Client VPN settings.
The VPN connectivity will not be established if you don't enable the Send all traffic over VPN connection option!
Windows 7
Currently only the following authentication mechanisms are supported:
- User authentication: Active Directory (AD), RADIUS, or Meraki hosted authentication.
- Machine authentication: Preshared keys (a.k.a., shared secret).
When using Meraki hosted authentication, VPN account/user name setting on client devices (e.g., PC or Mac) is the user email address entered in the Dashboard.
Open Start Menu > Control Panel, click on Network and Internet, click on View network status and tasks.
In the Set up a connection or network pop-up window, choose Connect to a workplace (Set up a dial-up or VPN connection to your workplace).
Choose Use my Internet connection (VPN), in the Connect to a workspace dialog window.
In the Connect to a Workplace dialog box, enter:
- Internet address: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- Destination name:This can be anything you want to name this connection, for example, 'Work VPN.'
Choose 'Don't connect now; just set it up so that I can connect later' option.
Click Next. In the next dialog window, enter the user credentials, and click Create.
Despite the name 'Unencrypted PAP', the client's password is sent encrypted over an IPsec tunnel between the client device and the MX. The password is fully secure and never sent in clear text over either the WAN or the LAN.
Windows 8
Currently only the following authentication mechanisms are supported:
- User authentication: Active Directory (AD), RADIUS, or Meraki hosted authentication.
- Machine authentication: Preshared keys (a.k.a., shared secret).
When using Meraki hosted authentication, VPN account/user name setting on client devices (e.g., PC or Mac) is the user email address entered in the Dashboard.
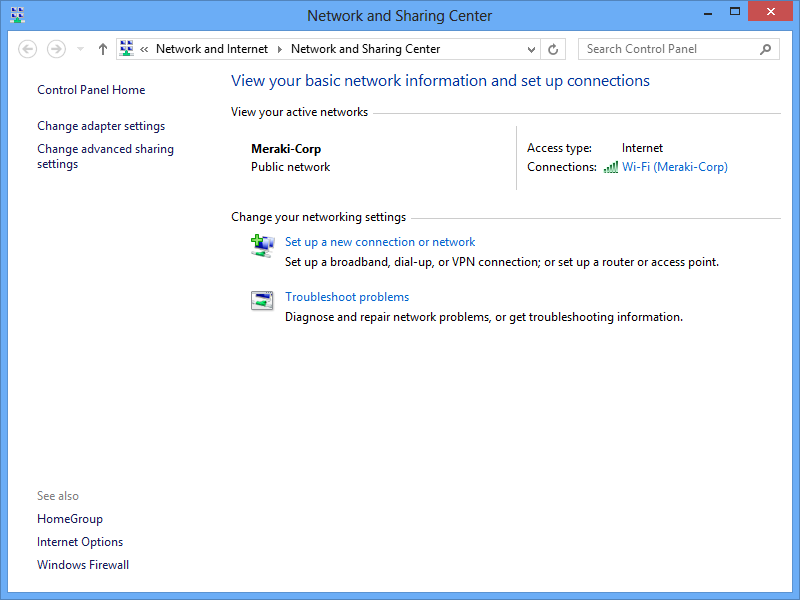
Open Start Menu > Network and Sharing Center and click Settings.
In the Set Up a Connection or Network pop-up window, choose Connect to a workplace.
(Set up a dial-up or VPN connection to your workplace).
Choose Use my Internet connection (VPN), in the Connect to a Workspace dialog window.
In the Connect to a Workplace dialog box, enter:
- Internet address: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- Destination name:This can be anything you want to name this connection, for example, 'Work VPN.'
Go back to Network and Sharing Center and click Change Adapter Settings.
Despite the name 'Unencrypted PAP', the client's password is sent encrypted over an IPsec tunnel between the client device and the MX. The password is fully secure and never sent in clear text over either the WAN or the LAN.
Windows 10
Currently only the following authentication mechanisms are supported:
- User authentication: Active Directory (AD), RADIUS, or Meraki hosted authentication.
- Machine authentication: Preshared keys (a.k.a., shared secret).
When using Meraki hosted authentication, VPN account/user name setting on client devices (e.g., PC or Mac) is the user email address entered in the Dashboard.
Open Start Menu > Search 'VPN' > Click Change virtual private networks (VPN)
From the VPN settings page, click Add a VPN connection.
In the Add a VPN connection dialog:
- VPN provider: Set to Windows (built-in)
- Connection name: This can be anything you want to name this connection, for example, 'Work VPN.'
- Server name or address: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- VPN type: Select L2TP/IPsec with pre-shared key
- User name and Password: optional
Press Save.
After the VPN connection has been created, click Change adapter options under Related settings.
Right-click on the VPN Connection from the list of adapters and click Properties.
Despite the name 'Unencrypted PAP', the client's password is sent encrypted over an IPsec tunnel between the client device and the MX. The password is fully secure and never sent in clear text over either the WAN or the LAN.
In Advanced Properties dialog box, choose 'Use preshared key for authentication' and enter the pre-shared key that admin created in Security appliance >Configure > Client VPN settings.
Back at the Network Connections window, right-click on the VPN connection and click Connect / Disconnect.
Find your VPN profile and click Connect.
Windows XP
Currently only the following authentication mechanisms are supported:
- User authentication: Active Directory (AD), RADIUS, or Meraki hosted authentication.
- Machine authentication: Preshared keys (a.k.a., shared secret).
When using Meraki hosted authentication, use the email address for VPN account / user name.
Open Start Menu > Control Panel, click on Network Connections.
In the Network Tasks section, click on Create a new connection.
Choose Connect to the network at my workplace, in the New Connection Wizard window.
Choose Virtual Private Network connection in the next section.
Then, give a name for this connection. This can be anything you want to name this connection, for example, 'Work VPN.'
Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
In the Connect <Connection Name> box, click on Properties
In the General tab, verify the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
Despite the name 'Unencrypted PAP', the client's password is sent encrypted over an IPsec tunnel between the client device and the MX. The password is fully secure and never sent in clear text over either the WAN or the LAN.
Since Client VPN uses the L2TP over IPsec standard, any Linux client that properly supports this standard should suffice. Please note that newer versions of Ubuntu do not ship with a VPN client that supports L2TP/IP, and will therefore require a 3rd party VPN client that supports the protocol.
Note: The xl2tp package does not send user credentials properly to the MX when using Meraki Cloud Controller authentication, and this causes the authentication request to fail. Active Directory or RADIUS authentication can be used instead for successful authentication.
Configuring Ubuntu 20.04
Ubuntu does not support L2TP VPN by default. You will need to install a couple of software packages to enable this functionality. The instructions below were written for Ubuntu 20.04 LTS with the Gnome desktop environment. Ubuntu versions 16.04 and 18.04 can be configured in a similar manner. However, due to the large number of Linux versions available, it is not feasible to document every supported Ubuntu version.

In order to begin the VPN setup, open up a terminal window. Do this by searching for Terminal in your application list. Click on the Terminal icon to open a new terminal session.
Once the terminal window appears, you will need to enter a few commands.
Note: You will need to be a part of the “sudoers” group to install these packages. If you receive an error message like “<username> is not in the sudoers file.” you will need to either adjust your permissions, contact your administrator to add your account as an administrator or have them install the software for you.
Once the packages have been installed, you may open up the Network Settings by searching for Settings in the application list, or by clicking on the Network icon at the top right of the screen and selecting Wired (or Wireless) Settings.
Once the Network Settings window pops up, you will see there is a VPN section listed. Click on the + icon to set up a new VPN connection.
Select the Layer 2 Tunneling Protocol (L2TP) VPN type on the modal pop up window. If L2TP is not listed as an option, please see the first step about installing the required packages.
After selecting the L2TP option, a new modal will pop up titled Add VPN. Fill out your VPN Name, Gateway, User name, and Password information here.
Meraki Vpn Ipad Mini
Note: To save your password on this screen, you must select the appropriate option from the question mark on the password field.
Meraki Vpn Ipad Software
Next, click on the IPsec Settings button to open the L2TP IPsec Options modal.
Once the modal pops up, expand the Advanced options, and enter the following:
Select OK to continue. You will be returned back to the Add VPN modal. Select the PPP Settings button.
On the L2TP PPP Options modal, select only the PAP authentication method. Be sure the other authentication methods are de-selected. All other options can remain as the default. Select OK to continue.
Select Add at the top right corner of the Add VPN modal to complete the VPN setup.
Now you may connect your VPN by toggling the button on the Network Settings page:
Or by selecting the Connect option from the top right corner menu.
Upon successful connection, a VPN icon will appear next to the network icon in the status bar.
Meraki Vpn Ipad Pro
Note: The version of network-manager-l2tp that is installed along with xl2tpd is known to cause issues when connecting to Meraki Appliances. To alleviate this, you must disable the xl2tpd service when using the network-manager GUI to connect to a Meraki VPN.
To stop the xl2tpd service once use this Terminal command:
sudo service xl2tpd stop
Meraki Vpn Ipad Download
To stop the xl2tpd service for all subsequent reboots use this Terminal command:
sudo update-rc.d xl2tpd disable
Meraki Vpn Ipad App
Some Supervised Feature Restrictions for iOS
Feature | Description | Supervision Required |
|---|---|---|
| Allow use of Camera | Show or hide the native camera app Allow or prevent use of the camera in all application | |
| Allow screen capture | Allow or prevent screenshots of the device's display | |
| Allow device assistant (Siri) | Allow or prevent use of Siri | |
| Allow Siri while locked | Allow or prevent Siri when device is locked | |
| Allow Voice dialing | Show or hide the native phone app Allow or prevent the use of the phone dialer | |
| Allow FaceTime calls | Allow or prevent FaceTime video calls | |
| Allow automatic sync when roaming | Allow or prevent device sync of managed data when device is roaming | |
| Allow Passbook notifications while locked | Show or hide Passbook notifications on the lock screen | |
| Allow in-app purchases | Allow or prevent buying extra content or subscriptions within an app | |
| Force user to enter iTunes Store password for all purchases | Require user to enter their iTunes store password to make purchases | |
| Allow multiplayer gaming | Allow or prevent gaming with multiple external users | |
| Allow adding Game Center Friends | Allow or prevent Game Center and integration in apps | |
| Show Control Center in lock screen | Show or hide Control Center while device is locked | |
| Show Notification center in lock screen | Show or hide Notification Center while device is locked | |
| Show Today view in lock screen | Show or hide Today View within Notification Center while device is locked | |
| Do not containerize work data and contacts from unmanaged apps | Allow or prevent data from being shared or stored in corporate (managed) apps in personal (unmanaged) apps | |
| Do not containerize personal data and contacts from managed apps | Allow or prevent data stored in personal (unmanaged) apps to be shared with corporate (managed) apps | |
| Allow Handoff | Allow or prevent apps from using Handoff capabilities | |
| Require passcode on outgoing AirPlay pairing requests | Require a passcode to broker an outbound Airplay request | |
| Require passcode on incoming AirPlay pairing requests | Require a passcode when an Airplay request is received | |
| Force paired Apple Watch to use Wrist Detection | Require paired Apple Watches to use wrist detection to automatically unlock or lock | |
| Disallow sharing of managed documents with AirDrop | Allow or prevent data from being shared or stored in corporate (managed) apps to AirDrop destinations | |
| Delay OS software updates | Delay updates to iOS for up to 90 days | |
| Allow UI configuration profile installation | Allow or prevent a UI prompt to install configuration profiles or certificates | |
| Allow modifying account settings | Allow or prevent the ability to add or remove accounts e.g. mail account, iCloud settings, iMessage settings, etc. | |
| Allow AirDrop | Allow or prevent AirDrop from being available | |
| Allow changes to cellular data usage for apps | Show or hide the toggle to allow apps to use cellular data | |
| Allow user-generated content in Siri | Allow or prevent Siri from showing content from sources that allow user-generated content e.g. Wikipedia | |
| Allow modifying Find My Friends settings | Allow or prevent changes to settings for the Find My Friends app | |
| Allow host pairing | Allow or prevent a device from pairing with Macs that do not have the Supervision certificate installed | |
| Enable Siri profanity filter | Allow or prevent profanity in Siri | |
| Allow configuring restrictions | Allow or prevent the end user from creating their own restrictions | |
| Allow Erase All Content and Settings | Allow or prevent the end user from being able to wipe a device | |
| Allow Internet results in Spotlight | Allow or prevent Spotlight search from showing internet search results | |
| Allow keyboard auto-correction | Allow or prevent word correction suggestions | |
| Allow keyboard spell-check | Show or hide warnings (red underline) underneath potentially mistyped words | |
| Allow definition lookup | Allow or prevent the ability to search for a word's definition by double-clicking a word | |
| Allow predictive keyboard | Allow or prevent the use of a predictive keyboard | |
| Allow keyboard shortcuts | Allow or prevent users to create and use keyboard shortcuts | |
| Allow pairing with Apple Watch | Allow or prevent an iPhone to pair with Apple Watch | |
| Allow modification of passcode settings | Allow or prevent users to change passcode on the device | |
| Allow modification of device name | Allow or prevent users to change the device's name | |
| Keep device name up-to-date with Dashboard | Sync the devices name to dashboard | |
| Allow modification of wallpaper | Allow or prevent changes to the device's wallpaper by the user | |
| Set Lock & Home screen wallpaper | Configure the lock screen and home screen wallpaper images | |
| Set lock screen payload | Set asset tag information and footnote to be displayed on the login window and lock screen | |
| Allow changes to Notifications settings | Allow or prevent end users to change notification preferences | |
| Allow remote screen observation by the Classroom app | Allow or prevent a Teacher iPad to view Student iPad screen in the Classroom App | |
| Allow modification of diagnostic submission and app analytics settings | Allow or prevent users from changing diagnostic log submission and app analytics settings | |
| Allow modification of Bluetooth settings | Allow or prevent users from changing Bluetooth settings | |
| Allow dictation input | Allow or prevent users from using voice to text | |
| Enforce SSID Whitelisting | Restrict the device to only connect to WiFi networks specified by MDM policy | |
| Allow creation of VPN configurations | Allow or prevent users to create new VPN configuration | |
| Enable USB Restricted Mode | Allow or prevent a device to connect to USB accessories without entering a passcode | |
| Enable Web Content Filter | Configure which HTTP or HTTPS websites via a permitted and block list | |
| Enable Global HTTP Proxy | Configure proxy settings for all HTTP/S network traffic | |
| Set managed email domains | The device will warn the user by coloring the email address text red if a user sends an email to an email domain not listed in a managed domains profile | |
| Set managed safari web domains | Documents viewed on or downloaded from managed web domains can only be opened by a managed app. | |
| Set home screen layout | Specific placement of app icons on the home screens | |
| Set Per App VPN | Create a VPN connector and create policies for when, how, and which applications or web pages would use this VPN connection | |
| Allow managed apps to write contacts to unmanaged contacts accounts | Allow or prevent contacts generated in managed apps to be created in unmanaged contacts accounts | |
| Allow unmanaged apps to read from managed contacts accounts | Allow or prevent contacts stored in managed contacts to be read by unmanaged apps | |
| Allow server-side Siri logging | Allows or prevent Siri from logging to its server | |
| Turn the Date & Time 'Set Automatically' feature to ON and disallow user disabling | Allow or prevent the user from changing the date and time settings Set the date and time on the device automatically | |
| Allow users to used saved passwords in Safari and AutoFill Passwords feature | Allow or prevent users from using saved passwords or the AutoFill password feature in Safari | |
| Allow user's device to request passwords from nearby devices | Allow or prevent a device from requesting passwords from other devices | |
| Allow users to share their passwords with the Airdrop Passwords feature | Allow or prevent a device from sharing passwords through AirDrop | |
| Allow users to add or remove a cellular plan to the eSIM of a device | Allow or prevent changes to the eSIM cellular plan | |
| Allow users to modify the personal hotspot setting | Allow or prevent the user from making changes to the hotspot settings |
